Articles - Support (5)
Time to Update Your Software and Operating System?
When you are focused on growing your business, staying up to date with software and operating system updates might not be at the top of your to-do list. However, neglecting these updates can have serious consequences for your organization. As Bret Arsenault, Chief Information Security Officer ...
Hybrid Workplaces Require New Security Measures
Hybrid workplaces are here to stay and the spectrum of office configurations requires a new approach to network security. Many companies are adapting by limiting their physical footprint with the use of “Flexwork Space.” Flexwork spaces are smaller, multi-purpose, cross-functional spaces and ...
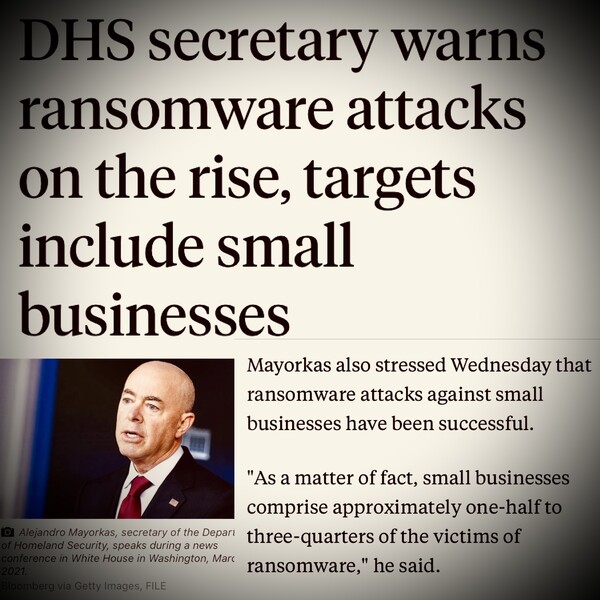
Small Businesses Are Ransomware Targets
Is your business too small to be targeted by ransomware? Unfortunately, bad actors are equal opportunity criminals, and do not discriminate about the size of their victims’ companies. In fact, many of these criminals target small businesses for exactly this reason. No business is too small. ...
Reasons to Use Small Business Cloud Solutions
Save Your Data Single-Handedly with Digital Storage With 94% of organizations using cloud services, data storage is arguably the most important part of any business—especially small to medium-sized businesses that are just getting started. Think of data storage as the brain behind your company. ...
Staying Safe From Phishing and Spear-Phishing
Do you know how to protect yourself against digital scams? Phishing – the practice of using email lures to fish for passwords, credit card numbers, and other personal information from a sea of users – has been around since 1996. Still, most people were not aware of the problem for five years until ...